In a world where bad actors employ increasingly sophisticated technologies to wreak havoc, organizations are looking beyond traditional perimeter approaches in favor of a Zero Trust strategy. Remote and hybrid work, increased reliance on managed services and third parties, and a rapidly evolving threat landscape comprise just some of the many reasons why traditional perimeter approaches to security consistently fall short. Traditional perimeter approaches create high-risk findings and limit an organization’s ability to detect, respond to, and recover from incidents. Because the perimeter is often seen as the area of highest risk to an organization—and the biggest business enablement prospect—many organizations begin their network modernization efforts by replacing their remote access VPN infrastructure.
Over the course of several years, the typical perimeter protection of a firewall with a remote access VPN approach has shifted to alternative approaches to protecting remote access to corporate networks and data. Technology leadership has recognized that it is no longer tenable to stand up a perimeter and enable remote access via overly permissive, non-identity-aware VPN connectivity. Instead, the industry is moving toward modernization via eclectic methods of deploying Zero Trust Network Access (ZTNA). The ZTNA approach is effective; however, efforts like ZTNA to modernize perimeter security are not a panacea.
Clarifying Zero Trust
Zero Trust is a misnomer. Zero Trust does not mean that there is no trust at all in an environment. Instead, Zero Trust means that there is no implicit trust. While NIST states “Never Trust, Always Verify,” in actuality, they are referencing the concept of least privilege. Least privilege means that a particular entity is given permissions to access only the data needed to perform a legitimate function.
ZTNA technologies typically control access to specific applications based on criteria defined in the control plane of the ZTNA technology. This type of control provides explicit access to specific types of applications in specific parts of the network. ZTNA technologies can only stop specific types of lateral movement and do not provide visibility into activity outside of application access. Often, other technologies that can be integrated to enable control and context provide more suitable alternatives.
When adopting ZTNA, many organizations claim they are adopting a Zero Trust strategy. They will highlight that they are enabling granular access control, visibility, and other Zero Trust tenets, while still primarily focusing on access and control at the network level. That’s not to say that VPN and network security modernization are not important. Instead, we must acknowledge that network security represents a fraction of Zero Trust strategy – meaning, Zero Trust strategies must take a holistic approach to applying controls, visibility, automation, and orchestration.
Understanding the struggle to adopt Zero Trust
In a recent report titled Strategic Roadmap for Zero Trust Security Program Implementation, Gartner outlined several reasons why organizations struggle to adopt or succeed with a Zero Trust strategy. One poignant observation of this report highlights the impact of increased operational requirements that Zero Trust controls can have on an organization, particularly when organizations fail to define privileges appropriately, and when they do not properly integrate technical controls to enable dynamically controlled authentication and authorization based on environmental and behavioral context.
I’d like to emphasize that Gartner calls out privileges, not a specific technology or the ability to control access. Essentially, Gartner notes that organizations struggle to implement Zero Trust because they are grappling with how to modernize their identity program. This finding demonstrates how identity is the often-overlooked foundation of a Zero Trust strategy. However, much like the rest of Zero Trust, identity is complex.
Prioritizing effective identity programs
Identity programs can be challenging to implement and manage. An effective identity program requires input and assistance from teams outside of technology and security, often creating brittle and manual touchpoints that lead to vulnerabilities in processes and procedures surrounding identity. These vulnerabilities often create a domino effect, causing issues with overprivileged accounts, MFA enablement, and other common identity gotchas, which then lead to challenges with the overall adoption of a Zero Trust strategy by limiting the integration of technical controls with appropriate authorization and context.
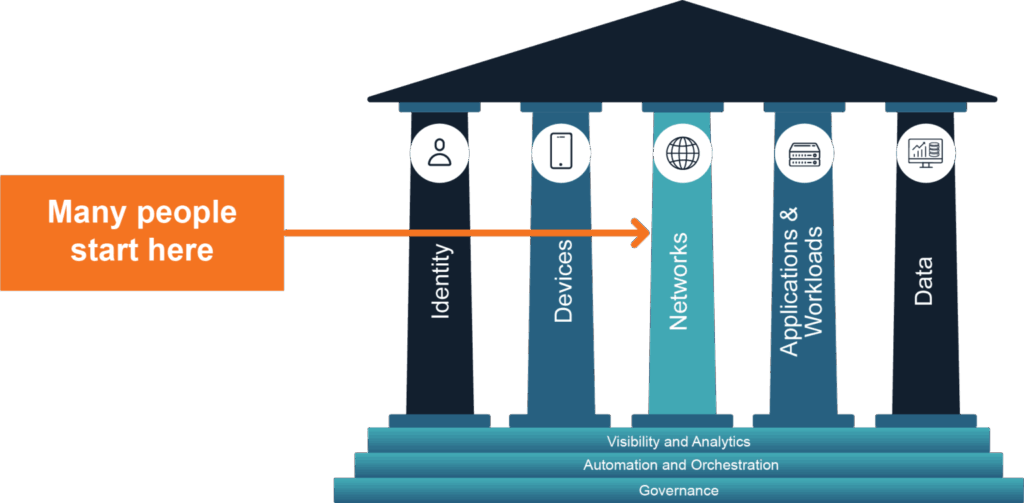
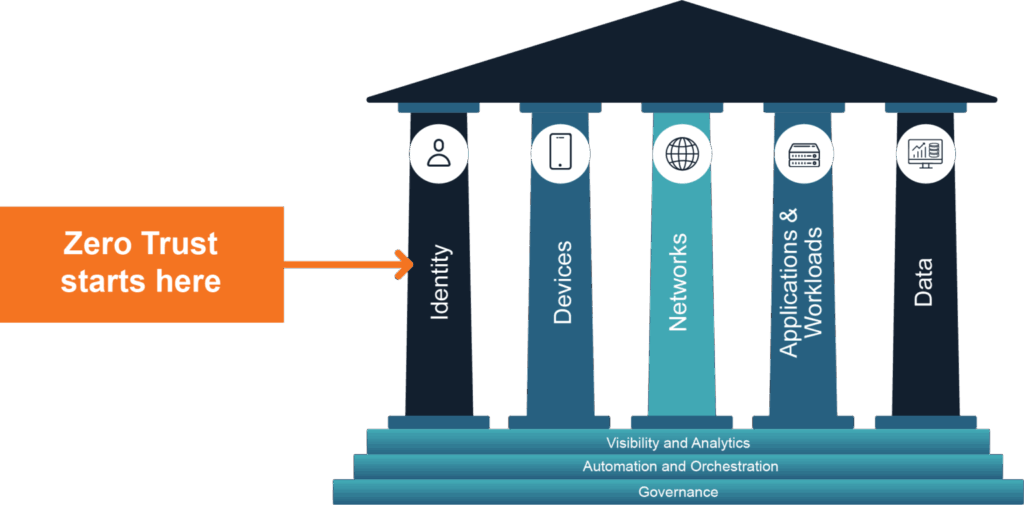
Illustration from NIST, Zero Trust Maturity Model (2023), https://www.cisa.gov/sites/default/files/2023-04/CISA_Zero_Trust_Maturity_Model_Version_2_508c.pdf
However, a well-run identity program drives control of other Zero Trust technologies. Firewall rules, micro-segmentation, ZTNA, data permissions, application permissions, observability, and other parts of Zero Trust rely on identity to run properly. Identity moves Zero Trust away from addressing “where should access be enabled” to addressing “who needs access to what.” By focusing on the “who” and “what” rather than the “where,” organizations can enable a truly useful and scalable Zero Trust strategy.
Additionally, by asking “who needs access to what,” the underlying technologies become a connectivity controlled by an identity control plane. Other technologies may feed information into the identity technology, but they are not making control decisions. Instead, identity technology enables access to decisions based on permissions granted to identities. These permissions may be automatically provisioned and deprovisioned, and subject to provisioning based on appropriate environment and contextual information.
5 steps for building your Zero Trust strategy
Wondering where to start with your Zero Trust strategy? Here are five steps you can take.
1. Define your strategy
Assemble your team: Create a team focused on the Zero Trust strategy. A solid Zero Trust strategy relies on input from a diverse team of stakeholders, the most common being networking, security, enterprise, and endpoint. Additionally, consider including stakeholders from executive management, legal, and business units as well as application owners to ensure alignment with business priorities.
Define policy: Document how, why, and where Zero Trust principles apply to the organization’s assets and user base.
2. Start small
Define use cases: Identify critical data and associated applications and systems that require security focus to create your use cases.
Prioritize: Choose Zero Trust use cases based on the business value and risk mitigation.
Use lessons learned: Zero Trust is an ongoing project; you will need to refine policies, tools, and workflows for broader implementation as progress is made.
3. Communicate with stakeholders
Educate users on Zero Trust: Users need to understand why changes are being made and their responsibilities during and after changes.
Get executive buy-in: Aligning initiatives to business objectives helps secure support for budget and organizational changes at the highest level.
4. Develop a governance framework
Define and enforce role-based access: Define set roles for access to help align identities to the resources users need to access.
Define lifecycle, access reviews, and audit documentation: Identity, and by extension, Zero Trust, relies on process and people to be successful. Creating frameworks, policy guidelines, and other documentation ensures you have the people and processes needed to support Zero Trust.
Update policies to adapt to threats and business: Organizations exist in environments where threats constantly shift and business requirements often change. Put processes in place to keep your policies current and aligned.
5. Build Zero Trust with identity-focused controls
Implement strong authentication: Use multifactor authentication (MFA) and/or passwordless authentication methods.
Adopt adaptive, context-aware authentication: Integrate technologies to share information to influence authentication and authorization decisions in near real time.
Use automation to monitor sessions and revoke sessions in real time: Long-standing sessions and compromised active sessions leave systems vulnerable.
Leverage technology to enforce Zero Trust: Here are a few examples:
- ZTNA to replace legacy VPNs
- Micro-segmentation within the network
- SWG and CASB at the Internet edge
Begin your Zero Trust journey with a complimentary GDT workshop
Adopting Zero Trust to secure your hybrid or remote workforce is a complex but worthy undertaking, helping your organization to meet compliance regulations and providing assurance that systems and data can be protected.
As a full-service IT provider, GDT takes a 360-degree approach to helping customers mature their security programs and adopt strategies like Zero Trust. We offer a complimentary half-day workshop with cybersecurity experts designed to explore your organization’s goals and challenges, identify gaps and capabilities, and provide a high-level roadmap with prioritized next steps to illuminate the path forward to Zero Trust. It’s a great opportunity that I highly recommend you check out.


