Fortune favors the prepared and preparing an incident response plan will position your company to survive attacks, limit damages and minimize the business disruptions that an inevitable successful attack can cause. Get your incident response team ready now. Read on!
Prepare for a Cybersecurity Incident
Today is a perfect day to prepare for a cybersecurity incident. Tomorrow may be too late. When you hear the axiom that it’s not a matter of “if” but “when” it may make you think someone is stoking fear, but it is wise to heed the warning and make sure that your organization has prepared to respond to incidents. Attacks should be assumed to be in process and ongoing with the potential of an incident looming.
A lot of attention is placed on the prioritization of the protections and defenses of technology resources with the hope that they will prevent successful attackers. However, in 100% of incident response cases I have been a part of the organization thought their protections would prevent the attack. In too few of them were the alarms acted upon in time to completely prevent the attack’s success.
How to prepare a custom incident response plan for your business.
What is an incident response plan?
An incident response plan is the plan for how the organization will be organized to respond to incidents. An incident response plan should not be looked at as the process that will be executed during an incident by a service provider only. Response playbooks are where the processes for analysis during the initial detection and identification occur. Steps for containment with decision workflows and pre-defined authorizations are part of mature SOC runbooks. In cases where automation is configured these types of aggressive containment measures can be the difference between a thwarted attack and catastrophic cybersecurity incident. These efforts and many others are the outcomes of incident response planning. But the incident response plan should consider big picture metrics, not the punch list of tasks to execute during an incident.
Incident Response Planning is the best investment you can make to protect your enterprise. Learn key insights in cybersecurity incident response preparation and how to implement a successful plan into your information security lifecycle.
How do I start my Incident Response Plan?
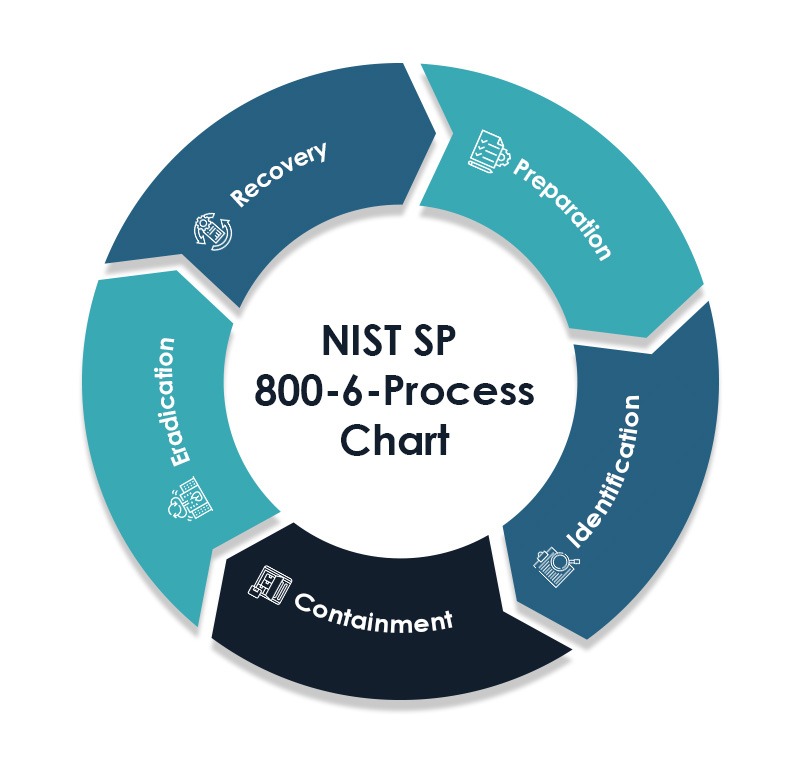
A good starting point for incident response planning is NIST Special Publication 800-61 revision 2 (NIST SP 800-61 or 800-61). The structure in NIST SP 800-61 for the incident response process is a solid reference model and defines 5 phases to focus efforts on. Below is a summary of each area as it relates to 800-61:
(Examples supporting the need for customization?)
NIST SP 800-61 is a good starting point and provides a useful framework for constructing an incident response plan, but unfortunately was last updated in 2012. A lot has evolved in that time, so if you are considering the DIY route of putting your incident response plan together here are some tips for leveling up from the fundamentals and including some essential improvements to the 800-61 considerations.

Preparing your incident response
NST SP 800-61 provides suggestions for gathering and organizing necessary or useful materials, tools and personnel as well as some security program aspects that could help prevent cybersecurity incidents from occurring. Keep in mind the items suggested are over 10 years old. To make sure your incident response program is ramped up beyond the fundamentals and to the levels needed to respond to today’s attacks and cyber threats, a significant focus on preparation is recommended.
Training and exercises, including table-top exercises (TTX), live-fire simulations and even combining red team attacks with blue team defending for purple team engagements are important to preparation. Keep in mind that exercises need to practice all parts of incident response from actively defending against the initial attack and penetration attempts, containment strategies to limit the success of the attacker, communication, escalation, external notifications, as well as considerations for recovery.
Working through all the phases of incident response is necessary to make sure that the organization is prepared. Borrow the lessons of athletes, fire fighters and military forces who spend a tremendous amount of time training for their professions to make sure that when game time, emergencies or real-world attacks occur, you too can be ready and prepared to execute the security tools and security measures in place.

Identification of elevated events in information security
800-61 includes detection and analysis of events that are elevated from monitoring processes and cybersecurity alerts as activities associated with identification. Precursors and indicators of attacks found in attack vectors corresponding to various categories of attack types (such as insider threats) along with severity levels based on impact are also topics covered.
Preparation activities associated with identification should include knowing what’s most important to you, where is it located, and how you can gain a leg up during an attack to cut adversaries off at the pass. Knowing where valuable data and the organization’s crown jewels reside, as well as key infrastructure, like where data backup, authentication, and remote access capabilities are performed is essential during an attack. Understanding where they are and the pathways through the network and protections is an advantage that the attacker won’t initially have.
Other things you can do prior to the onset of an attack is to establish your support system for information and intelligence. The ability to obtain information to identify adversaries and get a truer risk assessment before they even touch your network resources gives you even more time to ward off attacks and future incidents. Threat intelligence beyond indicators and IP addresses can be well worth the investment when it keeps attackers from successfully gaining access to data and systems.

Containment in response to cyber attacks
800-61 describes containment as decision-making from predetermined containment strategies that can be triggered and implemented in response to significant attack types. Isolating an infected system or blocking the activity from an identifiable source are basic and somewhat outdated for thwarting the tactics of current attackers. However, the concept is still valid for attacks that have achieved a level of infiltration. Containment measures still need to include cutting off the attackers at the pass. Isolating key systems, cutting off remote access or internet access at the earliest stages of significant attacks can be the difference between quick recovery and months of rebuilding.
Containment can be looked at like an Andon Cord, or the red stop button you see on manufacturing equipment. Preparing containment measures for various types of incidents in advance can be as simple as an isolation rule in a perimeter firewall, or a rule in the endpoint protection software. When signals indicate something is going wrong these containment measures can be executed to lock down the environment to limit damage, prevent attackers from gaining further access, or ensure that valuable data cannot be extracted from the organization in real-time. Using automation to execute these containment measures and security controls automatically can be risky but critical in terms of timing. In any case, working through the containment strategies and ensuring that under a set of conditions members of the security team are authorized and permitted to act without convening a committee can make a huge difference in your risk management. It is always easier to recover operations from a planned shutdown than it is after attackers have wreaked havoc on your systems and sensitive information.

Eradication of incidents and Recovery of systems
Eradication is described as removing all aspects of the incident and attacker activities from all affected systems and accounts. Eradication may in some cases require recovery steps to restore systems to clean and undamaged. Recovery is technically restoring systems and functionality to a state where business processes are reestablished. Recovery from a business perspective is getting to the place where the organization team members can once again conduct its affairs, perform its mission, and do the things that are associated with its purpose. Modernizing and leveling up the phases of eradication and recovery will be covered in more depth in an upcoming blog that focuses on Getting Back to Business after a cyberattack.

Moving forward with your Incident Response Plan
Preparation is the most important aspect of the Incident Response Plan, closely followed by continuous improvement (continuous readiness) that leverages lessons learned. Plan to focus on improvement with every exercise or actual incident. Take time at the conclusion to conduct incident reporting, often referred to as a “Hot Wash Session” or “Postmortem Review” to talk about root cause, what went well, what improvements are needed, and how to be better prepared next time.
Download our comprehensive Incident Response Preparation Checklist for a step-by-step guide to fortifying your organization’s defenses against cyber threats. Equip your team with the necessary tools and strategies to mitigate risks and ensure uninterrupted business operations. Get your free copy now!
Cybersecurity Solutions with GDT are the answer to your Security Incident Response Plan
Check in with the team here at GDT. We can help to modernize your plan and get your organization tuned up with preparations for the dynamics of cybersecurity attacks today and into the future. Our team can help facilitate preparedness with Incident Response Exercises that include Table-Tops (TTXs), simulations and Purple-Team engagement as well as conduct assessments of your cybersecurity program and information security capabilities.
Author
-
Brian Engle is the principal cybersecurity advisor at GDT. Brian has 25+ years of cybersecurity experience leading and guiding security and risk management programs and has delivered actionable roadmaps and executed plans for C-level leadership and tactical plans for all aspects of security operations and information security program management. Brian’s roles have included executive leadership at Apollo-IS and CyberDefenses for all aspects of professional service and managed service delivery of security operations, consulting, threat intelligence, security engineering, and program management. In addition, previous enterprise roles include CISO for the State of Texas and the Texas Health and Human Services Commission, Executive Director for the Retail Information Sharing and Analysis Center, and CISO for Temple-Inland.
View all posts




