By Richard Arneson
Who would have thought that by twisting fiber optics you could get speeds up to 100 times faster? Not me, but apparently engineers and researchers at Melbourne, Australia’s RMIT University thought it would. They wondered whether fiber, if twisted—or at least the light within it was twisted—could create another dimension, a third dimension, to carry 1’s and 0’s faster. Spoiler alert—it can.
Actually, it was U.S.-based researchers who first discovered that light could be “twisted”, but it was the ones from down under who first created a reasonable-sized detector to read the transmitted information. The first detector was the size of a Mini Cooper, but the chip has been whittled down considerably—it’s now the width of a single strand of human hair.
While it’s unclear if the U.S. researchers were inspired by the same vision, those at RMIT got the idea by looking at the double helix spiral in DNA. Both sets of researchers, however, pondered about the same thing—would increasing spirally light’s momentum (it’s called orbital angular momentum) could enhance transmission speeds?
The promise that twisted fiber holds is staggering. According to one (1) researcher who worked on and was eminently involved with the project, the amount of turns could be, theoretically, infinite.
Boost efficiency, upgrade easily
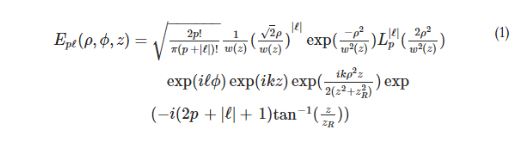
With fiber optics, pulses of light transmit the data, but the information can only be maintained through the light’s color, and it depends on whether it’s carried in a vertical or horizontal fashion. Twisting the light simply creates more travel space for the information within the fiber. This third dimension is like having a brand new HOV lane appear on the freeway overnight. And remember, twisting the fiber is a misnomer. It’s the light that’s twisted, which means today’s fiber optic networks could remain in place and untouched, whether buried or strung aerially. Each turn of the light produces a unique value, and the more turns, the faster the transmission speed.
Oh, and in case you’re champing at the bit wondering what the schematic structure of twisted light looks like, here it is…enjoy:
If you want to read RMIT’s research report—and see other formulas like this—it’s published in the journal Nature Communications.
If you have questions or would like more information about fiber optics or optical networking, contact GDT’s Optical Networking practice professionals at Optical@gdt.com. Composed of experienced optical engineers, solutions architects and project managers who specialize in optical networks, the GDT Optical Networking team supports some of the largest service providers and enterprises in the world. They’d love to hear from you.
For additional reading about fiber optics, check these out:
A fiber optic first
When good fiber goes bad
Busting the myths about fiber optics


